UNIX, OpenVMS and Windows System Administration, Digital Forensics, High Performance Computing, Clustering and Distributed Systems.
Monday, August 30, 2010
AIX 7.1 Open Beta
AIX 7.1 Open Beta is out
http://www-03.ibm.com/systems/power/software/aix/v71/index.html
Looks like you can backup / restore LPARS to wpars. Awesome!
Check out the IBM AIX Version 7.1 Differences Guide for details.
Email the author • Email this • Save to del.icio.us • Digg This! • Technorati Links
Posted by cmihai at 7:04 PM 3 comments ![]()
Sunday, July 18, 2010
Converting Perforce depots to Mercurial repositories with hg convert
Email the author • Email this • Save to del.icio.us • Digg This! • Technorati Links
Posted by cmihai at 10:56 PM 0 comments ![]()
Labels: Revision Control, UNIX
Tuesday, April 06, 2010
Share GNU screen sessions with a different user
Here's something cool you can do with screen. Share a screen session with multiple terminals. "screen -x". Of course, this only works if you're using the same user.
Email the author • Email this • Save to del.icio.us • Digg This! • Technorati Links
Posted by cmihai at 1:27 PM 3 comments ![]()
Labels: Open Source, UNIX
Sunday, January 03, 2010
Unpack functions and BSDProgress - progress bar for your archives.
A colored unpack script using bar:
A little KSH93 function for your .profile. Now you can augomatically unpack most archives while watching the pretty progress bar.
You need bsdprogress (Solaris and Linux port of NetBSD's progress). With a bit work it also works on AIX.
I just re-wrote this for progress, so I didn't check the cpio and such yet.
# Mihai Criveti - Unpack function:
# Progress Unpack - unpack using GNU tar and bsdprogress.
function up {
for archive in $*; do
print $archive;
case $archive in
(*.tar) progress -f $archive gtar xpif - ;;
(*.tar.gz) progress -f $archive gtar -zpixf - ;;
(*.tgz) progress -zf $archive gtar -ipxf - ;;
(*.tar.bz2) progress -f $archive gtar -jipxf - ;;
(*.tbz) progress -f $archive gtar -jipxf - ;;
(*.gz) progress -f $archive gunzip -;;
(*.bz2) progress -f $archive bunzip -;;
(*.tar.Z) uncompress -c $archive | tar gxvf - ;;
(*.cpio) cpio -icd < $archive ;;
(*.Z) uncompress $archive ;;
(*.rar) unrar x $archive ;;
(*.zip) unzip $archive ;;
esac
done
}
Let's say we want to unpack files that end in *bz2 (it will automagically detect .tar.bz2 or tbz2), *gz and a specific tar archive:
cmihai@phobos:/home/cmihai/build$ up g*bz2 c*gz Python\-3.0.1.tar
gnupg-1.4.10.tar.bz2
100% |**********************************************************************| 3330 KB 296.95 KB/s 00:00 ETA
gnupg-2.0.14.tar.bz2
100% |**********************************************************************| 3888 KB 340.20 KB/s 00:00 ETA
ccache-2.4.tar.gz
100% |**********************************************************************| 86363 201.51 KB/s 00:00 ETA
Python-3.0.1.tar
91% |******************************************************** | 43320 KB 787.63 KB/s 05:00 ETA
See: http://netbsd.gw.com/cgi-bin/man-cgi?progress++NetBSD-currenthttp://mac.freshmeat.net/projects/bsdprogress/It builds fine on AIX (Makefile tweaks), Solaris and Linux. Native on NetBSD.
Other versions:
http://clpbar.sourceforge.net/
http://freshmeat.net/projects/progress
Email the author • Email this • Save to del.icio.us • Digg This! • Technorati Links
Posted by cmihai at 4:09 AM 0 comments ![]()
Friday, February 13, 2009
Epoch Fail!
Epoch time 1234567890 is approaching fast, don't miss it!
cmihai@phobos:/home/cmihai$ date +%s
1234549466
cron your scripts so you don't miss it!
Email the author • Email this • Save to del.icio.us • Digg This! • Technorati Links
Posted by cmihai at 8:24 PM 0 comments ![]()
Labels: UNIX
Friday, February 06, 2009
UNIX colors and tools
Just opened a new package of colored chalk so I'll write on my blackboard :-).
Can't really have fun without:
- OpenSSH
- GNU screen
- KornShell 93, AWK, 1003.1 Shell & Utilities
- Emacs, ed
- Mutt
- Midnight Commander (mc)
- Elinks
- Terminus font (sure, it's not a tool, but it sure as hell helps , especially during those 20 hour debugging sessions).

256 colors _really_ do make quite a difference in Emacs (and vim) btw. Normal dtterm or xterm-color get you the first 8...

All you really need to do to get this working on AIX is to add a new TERMINFO entry (tic). You can easily grab the 256 color xterm with infocmp..
/usr/bin/tput colors
256

VIM looks pretty good too with a 256 color theme also (inkpot):

Email the author • Email this • Save to del.icio.us (3 saves, tagged: aix color colors) • Digg This! • Technorati Links
Posted by cmihai at 8:22 PM 2 comments ![]()
Thursday, January 15, 2009
Maximum login name lenght - Username too long in AIX 5.3
# useradd itssomeguy
3004-694 Error adding "itssomeguys" : Name is too long.
# getconf LOGIN_NAME_MAX
9
# lsattr −El sys0 −a max_logname
max_logname 9 Maximum login name length at boot time True
# chdev −l sys0 −a max_logname=18
sys0 changed
# reboot
Email the author • Email this • Save to del.icio.us (1 save) • Digg This! • Technorati Links
Posted by cmihai at 10:36 PM 2 comments ![]()
Saturday, May 24, 2008
Disable OpenSolaris Network Auto-Magic (NWAM)
NWAM is now enabled by default, but it has some limitations (only one NIC is enabled, etc). Personally, I like to configure the network interfaces myself.
To disable Network Auto-Magic on SXCE (Solaris Express Community
Edition) or Indiana (OpenSolaris):
# svcadm disable svc:/network/physical:nwam
Posted by cmihai at 1:05 PM 0 comments ![]()
Labels: Open Source, Solaris, Sun, UNIX
Thursday, May 15, 2008
Custom df (diskfree) column output in Solaris using nawk
Let's say you want to combine some features of "df -h" with "df -n" to show filesystem type and some other custom modifications to the output. This is where awk/nakw/gawk/whatever come in handy:
% df -g | nawk '{if (NR % 5 == 1) printf "%-22s", $1 ; if (NR % 5 == 4) printf "%-10s", "fstype " $1 "\n"; if (NR % 5 == 2) printf "%-30s",$1/2/1024/1024 " GB"; if (NR % 5 == 2) printf "%-30s", $4/2/1024/1024 " GB free "}'
| / | 33.6627 GB | 18.4351 GB free | fstype ufs |
| /devices | 0 GB | 0 GB free | fstype devfs |
| /system/contract | 0 GB | 0 GB free | fstype ctfs |
| /proc | 0 GB | 0 GB free | fstype proc |
| /etc/mnttab | 0 GB | 0 GB free | fstype mntfs |
| /etc/svc/volatile | 7.88214 GB | 7.8813 GB free | fstype tmpfs |
| /system/object | 0 GB | 0 GB free | fstype objfs |
| /lib/libc.so.1 | 33.6627 GB | 18.4351 GB free | fstype ufs |
| /dev/fd | 0 GB | 0 GB free | fstype fd |
| /tmp | 7.88142 GB | 7.8813 GB free | fstype tmpfs |
| /var/run | 7.88134 GB | 7.8813 GB free | fstype tmpfs |
| /export/home | 74.4858 GB | 1.87458 GB free | fstype ufs |
| /storage | 108.639 GB | 66.9259 GB free | fstype nfs |
You can also add a comma (,) to the separators and output > csv (you can open the comma separated values table in Excel or OpenOffice or any other Spreadsheet application) :-).
Posted by cmihai at 9:06 PM 3 comments ![]()
Labels: Open Source, Scripting, Solaris, UNIX
OpenBSD Web Portal server (Drupal)
Final goal: Drupal Web portal with TinyMCE JavaScript editor, Unicode and Locales support running on OpenBSD 4.3.
a. You can install OpenBSD via cdrom (install43.iso or cd43.iso for netinstall) or netboot via TFTP / BOOTP / DHCPD. Read diskless(8) for details. On Windows, you can use TFTPD32 for DHCP/TFTP.
b. Partition the disk (read the FAQ on partitioning). Example partitioning scheme:
| Partition | Mount location | Filesystem | Mount options | |
| /dev/sd0a | / | ffs | rw,softdep | 1 1 |
| /dev/sd0b | swap | swap | | |
| /dev/sd0c | Whole disk | | | |
| /dev/sd0d | /tmp | ffs | rw,softdep,nodev,nosuid | 1 2 |
| /dev/sd0e | /var | ffs | rw,softdep,nodev,nosuid | 1 2 |
| /dev/sd0f | /usr | ffs | rw,softdep,nodev | 1 2 |
| /dev/sd0g | /home | ffs | rw,softdep,nodev,nosuid | 1 2 |
c. Disable non-critical services (like ident, time, daytime, etc.) from /etc/inetd.conf. Just comment out the lines you don’t want with a #.
d. Make sure you enable Soft Updates (softdep) mounts – they increase the Filesystem performance tenfold when it comes to writing a lot of small files. This is done by adding “softdep” to mount options in /etc/fstab.
e. Add a regular user account. You can use the useradd(8) script. Make sure you add the user to the wheel group to allow su – root.
f. For added security configure „sudo” by running visudo(8). You can permit all users in the wheel group to sudo root: %wheel ALL=(ALL) NOPASSWD: SETENV: ALL
i. It’s usually best to disable root logins and use “sudo” for root access (sudo –i or su – if you need a root sheel). Edit /etc/ssh/sshd_config. You can also change the default ssh port from 22 to some random port to mitigate against brute force attacks. Keeps them from filling out your logs with junk. Consider using ssh keys also.
ii. Port 6969
iii. PermitRootLogin no
iv. Restart the OpenSSH daemon: „pkill –HUP sshd”
g. Configure your user profile to use a ftp mirror. Add the following to your ~/.profile: (or whatever shell you’re using, eg: .bashrc, .zshrc): PKG_PATH=ftp://ftp.su.se/pub/OpenBSD/4.3/packages/i386/; export PKG_PATH
h. Restart the system (to mount softdep, etc.).
i. Install some “critical” packages:
i. pkg_add -vi mc zsh screen elinks zip unzip bzip2
j. Install ports
i. cd /usr
sudo ftp ftp://ftp.su.se/pub/OpenBSD/4.3/ports.tar.gz
sudo tar zxf ports.tar.gz
k. Unpack the OpenBSD source code (src and kernel – sys) – these are required for patching OpenBSD:
i. cd /usr/src
sudo ftp ftp://ftp.su.se/pub/OpenBSD/4.3/src.tar.gz
sudo ftp ftp://ftp.su.se/pub/OpenBSD/4.3/sys.tar.gz
sudo tar zxvf src.tar.gz
sudo tar zxvf sys.tar.gz
l. Apply OpenBSD security patches. You download patches from http://www.openbsd.org/errata43.html and you apply them using the instructions in the patch headers:
i. ftp ftp://ftp.openbsd.org/pub/OpenBSD/patches/4.3.tar.gz
You can put 001_openssh.patch, 002_openssh2.patch and the following patches in /usr/src and apply them. Read the header for the patches for instructions.
% head -11 001_openssh.patch
Apply by doing:
cd /usr/src
patch -p0 < install ="="> lib
===> ssh
install -c -s -o root -g bin -m 555 ssh /usr/bin/ssh
install -c -o root -g bin -m 444 ssh.cat1 /usr/share/man/cat1/ssh.0
install -c -o root -g bin -m 444 ssh_config.cat5 /usr/share/man/cat5/ssh_config.0
/usr/share/man/cat1/slogin.0 -> /usr/share/man/cat1/ssh.0
/usr/bin/slogin -> /usr/bin/ssh
===> sshd
install -c -s -o root -g bin -m 555 sshd /usr/sbin/sshd
install -c -o root -g bin -m 444 sshd.cat8 /usr/share/man/cat8/sshd.0
install -c -o root -g bin -m 444 sshd_config.cat5 /usr/share/man/cat5/sshd_config.0
===> ssh-add
install -c -s -o root -g bin -m 555 ssh-add /usr/bin/ssh-add
install -c -o root -g bin -m 444 ssh-add.cat1 /usr/share/man/cat1/ssh-add.0
===> ssh-keygen
install -c -s -o root -g bin -m 555 ssh-keygen /usr/bin/ssh-keygen
install -c -o root -g bin -m 444 ssh-keygen.cat1 /usr/share/man/cat1/ssh-keygen.0
===> ssh-agent
install -c -s -o root -g _sshagnt -m 2555 ssh-agent /usr/bin/ssh-agent
install -c -o root -g bin -m 444 ssh-agent.cat1 /usr/share/man/cat1/ssh-agent.0
===> scp
install -c -s -o root -g bin -m 555 scp /usr/bin/scp
install -c -o root -g bin -m 444 scp.cat1 /usr/share/man/cat1/scp.0
===> sftp-server
install -c -s -o root -g bin -m 555 sftp-server /usr/libexec/sftp-server
install -c -o root -g bin -m 444 sftp-server.cat8 /usr/share/man/cat8/sftp-server.0
===> ssh-keysign
install -c -s -o root -g bin -m 4555 ssh-keysign /usr/libexec/ssh-keysign
install -c -o root -g bin -m 444 ssh-keysign.cat8 /usr/share/man/cat8/ssh-keysign.0
===> ssh-keyscan
install -c -s -o root -g bin -m 555 ssh-keyscan /usr/bin/ssh-keyscan
install -c -o root -g bin -m 444 ssh-keyscan.cat1 /usr/share/man/cat1/ssh-keyscan.0
===> sftp
install -c -s -o root -g bin -m 555 sftp /usr/bin/sftp
install -c -o root -g bin -m 444 sftp.cat1 /usr/share/man/cat1/sftp.0
===> scard
install -c -m 444 -o root -g bin Ssh.bin /usr/libdata/ssh
- 2. Restart the system to apply patches (or just the affected services by using pkill –HUP for example if you didn’t patch the kernel).
a. % cd / && sudo ftp ftp://ftp.su.se/pub/OpenBSD/4.3/i386/xbase43.tgz
% sudo tar xzvphf xbase43.tgz
a. % sudo pkg_add -vi php5-core php5-mysql php5-curl php5-mbstring php5-gd
Ambiguous: choose package for php5-gd
0:
1: php5-gd-5.2.5
2: php5-gd-5.2.5-no_x11
Your choice: 1
parsing php5-gd-5.2.5
b. Activate PHP modules by creating the various symbolic links:
i. % sudo ln -s /var/www/conf/modules.sample/php5.conf /var/www/conf/modules
ii. % sudo ln -fs /var/www/conf/php5.sample/curl.ini /var/www/conf/php5/curl.ini
iii. % sudo ln -fs /var/www/conf/php5.sample/gd.ini /var/www/conf/php5/gd.ini
iv. % sudo ln -fs /var/www/conf/php5.sample/mbstring.ini /var/www/conf/php5/mbstring.ini
v. % sudo ln -fs /var/www/conf/php5.sample/mysql.ini /var/www/conf/php5/mysql.ini
5. Install, configure and secure the MySQL database:a. % sudo pkg_add -vi mysql-server
b. Installing the default database
i. % sudo /usr/local/bin/mysql_install_db
c. Starting the MySQL service:
i. % sudo /usr/local/bin/mysqld_safe&
[1] 32390
% Starting mysqld daemon with databases from /var/mysql
d. Secure the installation (delete anonymous users, the test database and set a root password). PS: don’t use # in your password, there’s a bug in the script. Set that manually if you want.
i. % sudo /usr/local/bin/mysql_secure_installation
e. Tune some sysctl parameters for MySQL:
i. Edit /etc/sysctl.conf:
kern.shminfo.shmall=32768
kern.maxfiles=8192
ii. Apply the changes
% sudo sysctl kern.shminfo.shmall=32768
kern.shminfo.shmall: 8192 -> 32768
% sudo sysctl kern.maxfiles=8192
kern.maxfiles: 3580 -> 8192
iii. Add a mysql login in /etc/login.conf:
mysql:\
:openfiles-cur=1536:\
:openfiles-max=3096:\
:tc=daemon:
iv. % sudo cap_mkdb /etc/login.conf
6. Configure SSL (Secure Sockets Layer) for Apache mod_ssl (https). Generate a self signed certificate (or sign one) by reading ssl(8).a. % sudo openssl genrsa -out /etc/ssl/private/server.key 1024
% sudo openssl req -new -key /etc/ssl/private/server.key -out /etc/ssl/private/server.csr
% sudo openssl x509 -req -days 365 -in /etc/ssl/private/server.csr -signkey /etc/ssl/private/server.key -out /etc/ssl/server.crt
b. Test SSL support (lynx is ssl enabled):
% sudo apachectl startssl
% lynx https://localhost
a. Edit the Apache configuration file and setup PHP and server details /var/www/conf/httpd.conf
AddType application/x-httpd-php .php
ServerAdmin cmihai@website
DirectoryIndex index.html index.php
ServerName hostname(fqdn)
b. Configure PHP:
i. Edit the PHP config /var/www/conf/php.ini
upload_max_filesize = 12M
c. Test PHP:
ed /var/www/htdocs/index.php
a
Test PHP:
.
w
q
% lynx http://localhost/index.php
d. Configure Sendmail for supporting the Apache chroot[1]
% sudo pkg_add -vi mini_sendmail-chroot
parsing mini_sendmail-chroot-1.3.6p0
mini_sendmail-chroot-1.3.6p0: complete
% sudo mkdir -p /var/www/usr/sbin/
% sudo ln /var/www/bin/mini_sendmail /var/www/usr/sbin/sendmail
% sudo cp /bin/sh /var/www/bin
a. % sudo ed /etc/rc.conf
httpd_flags="-DSSL"
b. % sudo ed /etc/rc.local
if [ -x /usr/local/bin/mysqld_safe ] ; then
su -c mysql root -c '/usr/local/bin/mysqld_safe >/dev/null 2>&1 &'
echo -n ' mysql'
fi
# Crearea unui link pentru socketul MySQL in chrootul Apache
mkdir -p /var/www/var/run/mysql
sleep 5
ln -f /var/run/mysql/mysql.sock /var/www/var/run/mysql/mysql.sock
c. Reboot to test changes.
9. Crate a database for Drupal and a user. Grand permissions:a. % sudo mysql -u root -p
CREATE USER drupal IDENTIFIED BY 'password';
CREATE DATABASE drupal CHARACTER SET utf8;
GRANT ALL PRIVILEGES ON drupal.* to USER drupal@localhost IDENTIFIED BY 'password';
a. % sudo pkg_add -vi drupal5-tinymce drupal5-link-to-content drupal5-imce drupal5-image drupal5-backup-migrate drupal5-autolocale drupal5-token drupal5-securelogin ImageMagick
11.Optionally configure .httauth for security:a. % cd /var/www
% sudo htpasswd -c htpasswd username
Add .htaccess to /var/www/htdocs
AuthName "Nu este permis accesul"
AuthType Basic
AuthUserFile ../htpasswd
require valid-user
b. Add “Add AllowOverride All” în /var/www/conf/httpd.conf.
c. Restart Apache (apachectl stop && apachectl startssl).

You can now configure Drupal and the various modules. Be sure to setup a backup schedule. You can use the Drupal database backup and restore module.
You can also install Apache mod_security for additional security:
% sudo pkg_add -vi modsecurity-apache
% sudo /usr/local/sbin/mod_security-enable
% sudo apachectl stop && sudo apachectl startssl
Make sure you read /usr/local/share/doc/mod_security/modsecurity-manual.pdf
You should also keep an eye on your webserver. For monitoring, I recommend top(1), vmstat, (8), sysctl hw, pftop and mytop.
% sudo pkg_add -vi mytop pftop
% sudo /usr/local/sbin/pftop
To use mytop you'll need a ~/.mytop file (and set proper permissions on it). You can add something like:
prompt=1
pass=
user=drupal
db=drupal
delay=5
port=3306
socket=
batchmode=0
header=1
color=1
idle=1
% mytop

MyTOP in Action
You'll also want to setup Packet Filter. Read the PF User's Guide, pf.conf(5) and the example rulesets in /usr/share/pf/examples. Enable pf in /etc/rc.conf (pf=YES).
[1] Read chroot(2) ssl(8) afterboot(8), etc.
Posted by cmihai at 5:15 PM 2 comments ![]()
Labels: BSD, Databases, Networking, Open Source, Security, UNIX
Thursday, May 01, 2008
OpenBSD 4.3 has been released
OpenBSD 4.3 has been released.
Posted by cmihai at 12:07 PM 0 comments ![]()
Labels: BSD, Open Source, UNIX
Wednesday, April 30, 2008
Convert NRG images to ISO images (nrg2iso) using dd
If you want to convert Nero "nrg" images to ISO format to mount or burn you can either use nrg2iso, or just use dd to skip the 300k header (will work just fine for DAO images):
dd if=image.nrg of=image.iso bs=4096 skip=75
Posted by cmihai at 7:30 PM 2 comments ![]()
Thursday, April 17, 2008
Solaris 10 update 5 Released
Solaris 10 5/08 has been released.
Posted by cmihai at 11:27 AM 0 comments ![]()
Labels: Enterprise, Solaris, Sun, UNIX
Friday, April 11, 2008
Project Etude - The Solaris 8 Migration Assistant now free
Project Etude - that lets you run Solaris 8 Containers (Zones) is now free.
Announcement here. Solaris 9 containers will also be available.
The project has been renamed into Solaris 8 Migration Assistant.
Posted by cmihai at 3:21 PM 0 comments ![]()
Labels: Solaris, UNIX, Virtualization
Tuesday, March 25, 2008
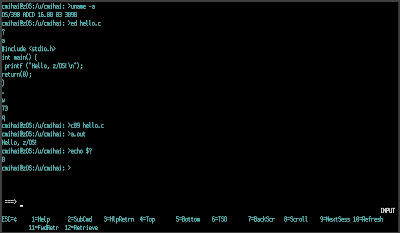
C Programming under Tru64 UNIX
A crash course in C programming under Tru64 UNIX :-). You've got a text editor - ed(1), of course, make(1), install(1) and a C compiler - cc(1) - and you're good to go.
Don't like ED? Well, Tru64 also comes with vi and XEmacs by default, so no worries.
All you need to do now is write a Makefile:
% ed Makefile
a
CC=cc
hello: hello.o
$(CC) -o $@ $<
hello.o: hello.c
$(CC) -c -o $@ $<
clean:
rm -f hello hello.o
.
w
q
% make
cc -c -o hello.o hello.c
cc -o hello hello.c
% ls
Makefile hello hello.c
% hello
Hello, Tru64 UNIX!
% make clean
rm -f hello hello.o
% ls
Makefile hello.c
Posted by cmihai at 2:09 AM 2 comments ![]()
Labels: Software Development, Tru64, UNIX
Monday, March 24, 2008
Building Git Version Control System on AIX, HP-UX and Solaris
Git is a fast version control system originally designed for the Linux kernel and written by Linus Torvalds.
Need git on AIX or HP-UX? Here's how:
HP-UX PA-RISC 2.0:
First, you're going to need a compiler (GCC), GNU make (gmake) and GNU coreutils (install). swinstall the dependency repositories first:
coreutils 6.9 coreutils
gcc 4.2.3 gcc
libgcc 4.2.3 libgcc
libiconv 1.12 libiconv
make 3.81 make
perl 5.8.8 perl
zlib 1.2.3 zlib
Untar the package and start building:
$ ./configure --with-iconv=/usr/local/bin
Edit the Makfile:
CC = gcc
AR = ar
RM = rm -f
TAR = tar
FIND = find
INSTALL = /usr/local/coreutils/bin/install
# sudo gmake NEEDS_LIBICONV=1 NO_TCLTK=1 install prefix=/usr/local
$ which git
/usr/local/bin/git
$ uname -sr
HP-UX B.11.11
$ git --version
git version 1.5.4.4
Building GIT on AIX 5.3 POWERPC:
Install dependencies and GCC, gmake, GNU coreutils (install), etc:
gcc-4.0.0-1 libgcc-4.0.0-1 libstdc++-4.0.0-1 libstdc++-devel-4.0.0-1 gcc-c++-4.0.0-1 readline-4.3-2 readline-devel-4.3-2 zlib-1.2.3-3 zlib-devel-1.2.3-3 make-3.80-1 unzip-5.51-1 flex-2.5.4a-6 bison-1.875-3 popt-1.7-2 gettext-0.10.40-6 expect-5.42.1-3 tcl-8.4.7-3 tk-8.4.7-3 coreutils-5.2.1-2
$ ./configure
vi Makefile:
CC = /opt/freeware/bin/gcc
AR = ar
RM = rm -f
TAR = /opt/freeware/bin/tar
FIND = find
INSTALL = /usr/linux/bin/install
RPMBUILD = rpmbuild
TCL_PATH = /opt/freeware/bin/tclsh
TCLTK_PATH = /opt/freeware/bin/wish
# gmake NO_MSGFMT=1 install prefix=/opt/freeware
$ uname -a
AIX aix 3 5 004518FC4C00
$ which git
/opt/freeware/bin/git
$ git --version
git version 1.5.4.4
Solaris 10:
Solaris 10 comes with gcc, gmake and GNU tools in /usr/sfw/bin, but you'll need ginstall from GNU coreutils (you can get it from Solaris Freeware).
$ ./configure
Edit the Makefile - set the path to "ar", "gcc" and GNU "install".
CC = /usr/sfw/bin/gcc
AR = /usr/ccs/bin/ar
RM = rm -f
TAR = tar
FIND = find
INSTALL = /opt/sfw/bin/install
Look for ifeq ($(uname_S),SunOS) and set INSTALL to /opt/sfw/bin/install also.
# gmake NO_TCLTK=1 NO_CURL=1 install prefix=/opt/sfw
% uname -a
SunOS ibmsolaris 5.10 Generic_127112-11 i86pc i386 i86pc
% git --version
git version 1.5.4.4
Posted by cmihai at 2:34 PM 9 comments ![]()
Labels: AIX, HP-UX, Open Source, Solaris, UNIX
Wednesday, March 12, 2008
IBM z/OS - OS/390 UNIX on zSeries Mainframe Development - C89
Posted by cmihai at 4:31 AM 0 comments ![]()
Labels: Mainframe, MVS, OS/390, Software Development, UNIX, z/OS
Sunday, March 09, 2008
ES40 - OpenSource Alpha AXP Emulator

I've already posted about other free Alpha or VAX emulators like PersonalAlpha (the free version of CHARON-AXP, also makers of CHARON-VAX) and SIMH. Now it's time for something open source, that will work on Windows and UNIX systems.
AlphaServer ES40 Emulator is a portable emulator for the HP (DEC, Compaq) AlphaServer ES40. The current version is capable of running OpenVMS with some limitations. The goal is to have a drop-in replacement for real ES40's. Emulates the Alpha AXP EV68CB processor and other devices.
Now you can run OpenVMS or Tru64 UNIX on your own personal computer.
The advantage of ES40 over PersonalAlpha is that you can emulate EV68 CPUs and a more modern system (AlphaServer ES40) and additional hardware. It's also open source, and will run on your Windows, Linux and UNIX machines. The problem is, it's no match for CHARON-AXP or PersonalAlpha in terms of performance.
You can even use ES40 to install other operating systems like BSD and Linux on Alpha.
Here's FreeBSD/alpha 6.3-RELEASE

Posted by cmihai at 11:29 PM 0 comments ![]()
Labels: Open Source, OpenVMS, UNIX, Virtualization
Tuesday, March 04, 2008
VPNC - Open Source client for Cisco VPN Contentrator
Got an ASA, a PIX or some other VPN Concentrator (or even Juniper NetScreen)? Well, you'll run into some troubles sooner or later. The Cisco VPN Client doesn't support 64 bit Windows clients, x86 Solaris clients and is just a pain to use on Linux.
VPNC doesn't require any kernel modules. Just put the IPSec gateway IP, IPSec ID, IPSec secret and XAuth username into /etc/vpnc/default.conf and start vpnc. It should work instantly :-). No fuss, no mess.
It will work just fine on Solaris, Linux, MacOS X or BSD machines. You can even get it running on your Windows box (Cygwin libs).
Posted by cmihai at 7:54 PM 0 comments ![]()
Labels: Cisco, Networking, Open Source, Security, UNIX
Saturday, March 01, 2008
Tunneling over ICMP, DNS, HTTP and HTTPS proxies
Stuck beyond a firewall, captive portal or proxy and need your ssh (or any other service)? Here's a few ways to tunnel out:
- PTunnel - Tunnel TCP using ICMP echo request and reply packets (PING), includes authentication, allows for multiple connections.
- Iodine - tunnel IPv4 data through a DNS server, allows for authentification.
- NSTX - Tunneling network packets over DNS.
- Corkscrew - tunneling SSH through HTTP proxies.
- httptunnel - bidirectional virtual data connection tunnelled in HTTP requests.
- gotthard - ssh through https proxy tunnel
Posted by cmihai at 5:46 PM 0 comments ![]()
Labels: Networking, Security, UNIX
About Me
- Mihai Criveti
- UNIX and VMS technologist, network and system administrator, SOA specialist, DBA.
Labels
- AIX (10)
- Backup (8)
- BOFH (20)
- BSD (20)
- Cisco (7)
- Clustering (9)
- Cryptology (9)
- Data Mining (1)
- Databases (12)
- DB2 (1)
- Debugging (13)
- Digital Forensics (29)
- Documentation (1)
- Elisp (1)
- Emacs (1)
- Enterprise (24)
- Graphics (3)
- Hardware (13)
- HP-UX (6)
- HPC (3)
- IBM (6)
- Internet (44)
- Java (1)
- LDAP (1)
- Linux (25)
- Mac (2)
- Mainframe (5)
- Malware analysis (6)
- Media (2)
- Microsoft (73)
- MVS (1)
- Networking (33)
- Open Source (100)
- OpenSolaris (11)
- OpenVMS (18)
- Oracle (13)
- OS/2 (1)
- OS/390 (1)
- QNX (3)
- Reverse Engineering (1)
- Revision Control (1)
- Scripting (24)
- Security (54)
- Software Development (24)
- Solaris (67)
- Sun (43)
- Tru64 (2)
- UNIX (48)
- Vim (1)
- Virtualization (37)
- Vulnerability Assessment (1)
- z/OS (1)

Business Intelligence Analyst
ReplyDeleteSQIAR (http://www.sqiar.com/services/bi-strategy/) is a leading Business Intelligence company.Sqiar Provide business intelligence Services Which help the company to present Information in Meaningful form.